Table of Contents
LANTIME: Configuring TACACS Authentication
TACACS is an external authentication method. It is supported with LANTIME firmware V6 and newer.
Configuration through the LANTIME WebUI
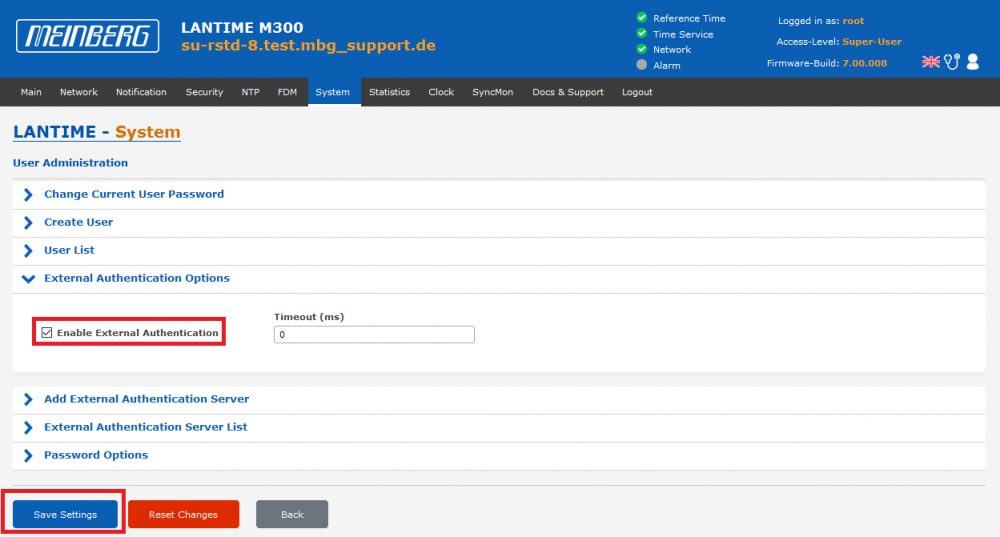
1. External authentication needs to be enabled first. This can be done on the System page –> User Management –> User Administration –> External Authentication Options:
2. Click Save Settings.
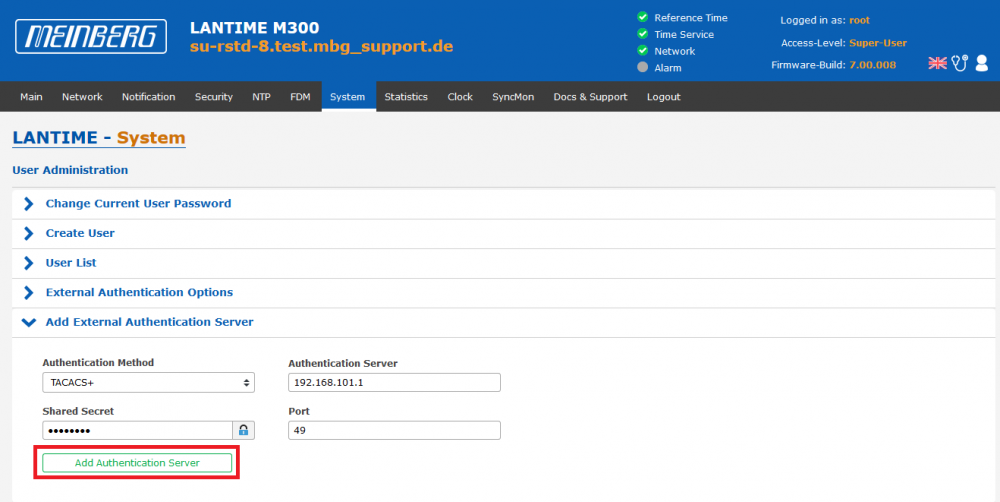
3. The TACACS server itself has to be configured under System page –> User Management –> User Administration –> Add External Authentication Server:
4. Fill out the form above and click Add Authentication Server.
What needs to be done on the TACACS Server?
The LANTIME TACACS authentication feature requires that each account that should be able to login to the LANTIME needs a special attribute called priv-lvl. This attribute has to be configured on the TACACS server. In addition you need to assign a value for this attribute for each TACACS user account. Possible values are: '100' (=Super User), '200' (=Admin User) or '300' (=Info User).
Troubleshooting
If the authentication is not working, there are several possible reasons:
- The configured shared secret on the LANTIME does not match the one on the TACACS server.
- The LANTIME is not in the same network subnet as the TACACS server, and no default gateway has been configured in the LANTIME WebUI under –>
Network–>Default Gateways. Due to the missing gateway, the LANTIME is unable to send the authentication request to the configured TACACS server. - The
priv-lvlattribute is missing in the authentication response sent by the TACACS server. The LANTIME is therefore unable to map the user correctly.
Configuration Examples
Linux tac_plus Server
Example /etc/tacacs+/tac_plus.conf configuration file with 1 Super-User account named tacacs_su, 1 Admin_User account named tacacs_au, and 1 Info-User account named tacacs_iu:
# This is the shared secret that clients have to use to access Tacacs+
key = "meinberg"
# User Groups
group = lantime_super_user {
service = lantime_mgmt {
priv-lvl = 100
}
}
group = lantime_admin_user {
service = lantime_mgmt {
priv-lvl = 200
}
}
group = lantime_info_user {
service = lantime_mgmt {
priv-lvl = 300
}
}
# User
# LANTIME Super User
user = tacacs_su {
member = lantime_super_user
pap = cleartext "tacacs_su" # User Password
}
# LANTIME Admin User
user = tacacs_au {
member = lantime_admin_user
pap = cleartext "tacacs_au" # User Password
}
# LANTIME Info User
user = tacacs_iu {
member = lantime_info_user
pap = cleartext "tacacs_iu" # User Password
}
Cisco ACS 5.X
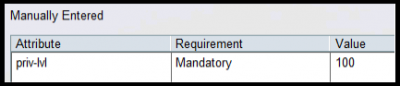
On a Cisco ACS 5.X authentication server, a new device type, a new access policy and a new shell profile with parameters below need to be created:
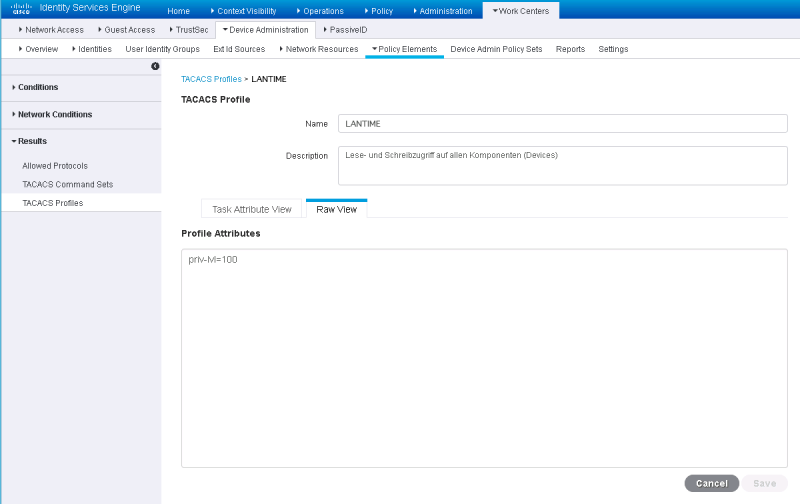
Cisco ISE
Further Assistance
If further assistance is required, contact Meinberg Technical Support: https://www.meinbergglobal.com/english/support/tech-support.htm
— Manuel Schäfer manuel.schaefer@meinberg.de, last updated 2023-05-16